SMS marketing is one of the fastest and most reliable ways to communicate with customers. Most brands use it to send offers, updates, reminders, OTPs, alerts, delivery messages, and more. As SMS offers a 98% open rate and a 45% response rate, it’s more effective than other communication channels like email and social media ads. The problem that most businesses miss is that their SMS campaigns fail because messages reach the wrong type of phone numbers.
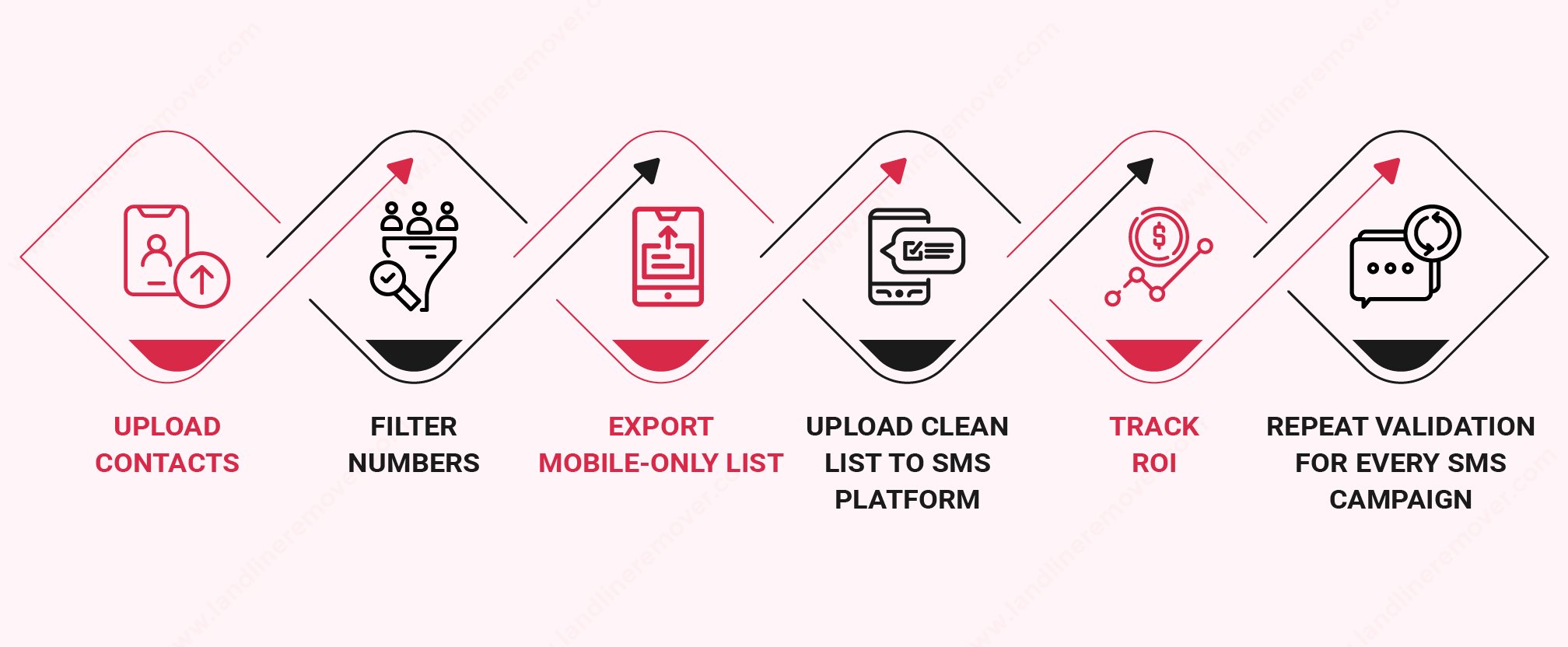
If you send thousands of texts and half of them reach landlines, VoIP-only numbers, or invalid contacts, your marketing budget disappears without results. However, accurate line-type detection changes everything. It helps you validate phone numbers, filter out landlines, and target only mobile users who can actually receive messages. Studies show that if you have a healthy SMS list, you will experience an opt-out rate between 0% to 1.5%
This blog sheds light on how line type detection works and how it boosts your SMS marketing ROI.
What is Line Type Detection?
Every phone number belongs to a specific category, which is known as the phone line type. A system that identifies these categories is called line type detection.
Here are some common phone line types.
| Phone Line Type | Can It Receive SMS? | Used For |
| Mobile | Yes | Personal texting, marketing, OTP |
| Landline | No | Office phone systems, home phones |
| VoIP | Sometimes | Business calling, customer support |
| Toll-Free Numbers | No | Support centers, IVR |
| Virtual Numbers | Limited | Apps, chat services |
A phone number validation and line type detection tool, like Landline Remover, scans the contact list and instantly classifies each number into the specific categories. It is crucial because only mobile numbers can receive marketing SMS. Therefore, if you send SMS to landlines or invalid VoIP numbers, you will waste your marketing budget and time, and ultimately, it will reduce campaign performance.